Simple passwords are often the bane of a business’ existence. If you routinely use strings like Password, 123456, Guest, or Qwerty to secure an account, then you need to reexamine your password practices before they lead to a data breach. A good password can go a long way toward helping you in this effort.
Argentum IT LLC Blog
Remote work on a widespread scale was introduced in less-than-optimal circumstances, but that doesn’t mean that today’s businesses shouldn’t use it to their full advantage. Let’s discuss the situation at hand, more specifically, a few ways you and your organization can support your team as they work remotely.
How many of your employees do you think hold a second job? This isn’t a particularly outlandish concept, but one thing that has come about as a result of the COVID-19 pandemic and its surge of remote work is that some employees hold two jobs at the same time, and not in the way that you might expect.
No matter how well you protect your network, chances are you’ll suffer from some vulnerability or another. That said, you can take considerable measures toward protecting your business so you don’t have to worry so much about them. Let’s discuss how your efforts today can protect your business now and in the future.
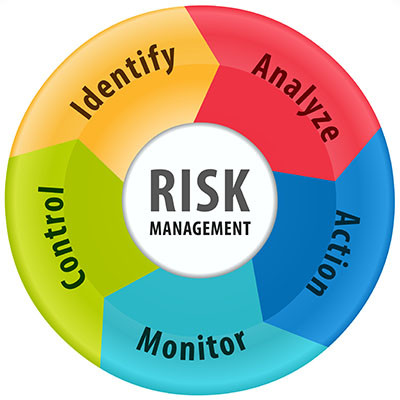
We’ve been known to take a bit of an extreme approach to cybersecurity—your business is at constant threat of being attacked by all manners of threats and all that. While we stand by this approach as an effective way to boost awareness and adherence to cybersecurity needs, there are certain attacks that are more likely to target you. This is where risk management comes into play.
There are many different varieties of cybercrime that businesses need to be vigilant about. However, most of these varieties can largely be avoided through a few basic practices and behaviors. Here, we’re giving you a few tips to help you prevent attacks from successfully influencing your business, so make sure you share them with your entire team, as well.
Keeping a secure password is a little confusing these days, especially when the standards for what is an acceptable, complex password seem to keep shifting back and forth. Let’s take a look at some of the industry-standard best practices for passwords and how you can implement them for your business.
The holiday season has a variety of famous key players, including the likes of Santa, Rudolph, and the rest of the North Pole crew. Each year, they use their magic to help spread goodwill and joy to all the nice children of the world… but did you know that they are also responsible for protecting those who make the naughty list from Santa’s villainous counterpart, Krampus?
As the official managed service provider for Santa’s operation, we have been cleared to share the story about how we’ve helped defy Krampus to save Christmas.
There’s no way around it; ransomware is bad stuff, plain and simple. The first half of 2021 saw a massive increase in ransomware attacks that made the lives of countless individuals and business professionals difficult. However, a new trend is surfacing, and it’s one that you might be surprised to see: fake ransomware threats.
As a business owner, you have a lot on your plate. Therefore, improving your productivity and streamlining how you spend your time while in the office is of paramount importance. With a simple four-step process, you can make your daily tasks so much easier to manage and, by extension, your business as a whole. Here are four tips that you can apply to your daily routine to improve your productivity during the workday.
Phishing is one of those threats that has been around for a long time, and as time passes by, these threats only become more difficult to identify. Some businesses can’t tell the difference between phishing scams and actual emails. Here’s how your company can take steps toward properly identifying and responding to phishing emails.
A lot of people spend the modern workday with headphones on or earbuds in, listening to music as they work or communicating through a headset. That makes it inevitable that these devices will get dirty. Let’s go over how these devices can be safely cleaned to get rid of the grime that nobody wants to be wearing on their head.
Cloud computing has been a godsend for many businesses by providing the flexibility and scalability they need to grow and enhance their offerings. Cloud computing, of course, also provides some capital cost reduction. There is no question that the cloud brings plenty of benefits to companies small or large, they now have the ability to pay per month for the computing resources they were making hefty capital investments for not too long ago; and, by-in-large, these investments pay off.
Workplace burnout is a serious issue that can have far-reaching impacts in your business. Therefore, it is critical that you can identify when one of your team members is starting to feel it, and know what you can do to help reduce it. Let’s go over what can lead to burnout, as well as a few ways to remediate it.
We’ve all been in a place where the storage on our computer fills up a little too quickly for our liking. While you could delete or store unused files in the cloud, there is another method that you can use to quickly free up a little extra space that you might not have realized is there. If you can delete temporary files, you might find that you suddenly have a lot more storage space to play around with on your computer.
While the right IT solutions can be a major benefit to your business and its processes, this will only be the case if your team members are trained to use them correctly. Let’s go over some of the training that you need to prioritize in order to ensure your team is ready to use your technology the way it should be used.